
White Paper
Introduction
For more than one hundred years, from the start of World War I in 1914 through Russia’s full-scale illegal invasion of Ukraine in 2022, airspace supremacy in battle, was defined by the nation with the most advanced crewed aircraft and the best-trained pilots. These platforms were expensive, built to last, and financially painful to lose. That model no longer holds. Uncrewed Aerial Systems (UAS) — cheap, autonomous, and increasingly stealthy — are rewriting the rules of modern warfare. Drones require no runways, no hangars, nor flight crews, and in some cases, no pilots at all. They can be launched from parked trucks, flown from outside national borders, and even controlled remotely from thousands of miles away.
Two recent operations underscore how decisively drones have upended traditional air defense. First, on 1st June, 2025, Ukraine’s “Spider’s Web” operation deployed 117 explosive drones concealed in cargo trucks deep inside Russia. These drones destroyed nuclear-capable bombers across five regions, inflicting an estimated US$7 billion in damage. With an operational cost of roughly US$234,000, this is a stark illustration of how an inexpensive drone can disable or destroy a US$100 million aircraft.
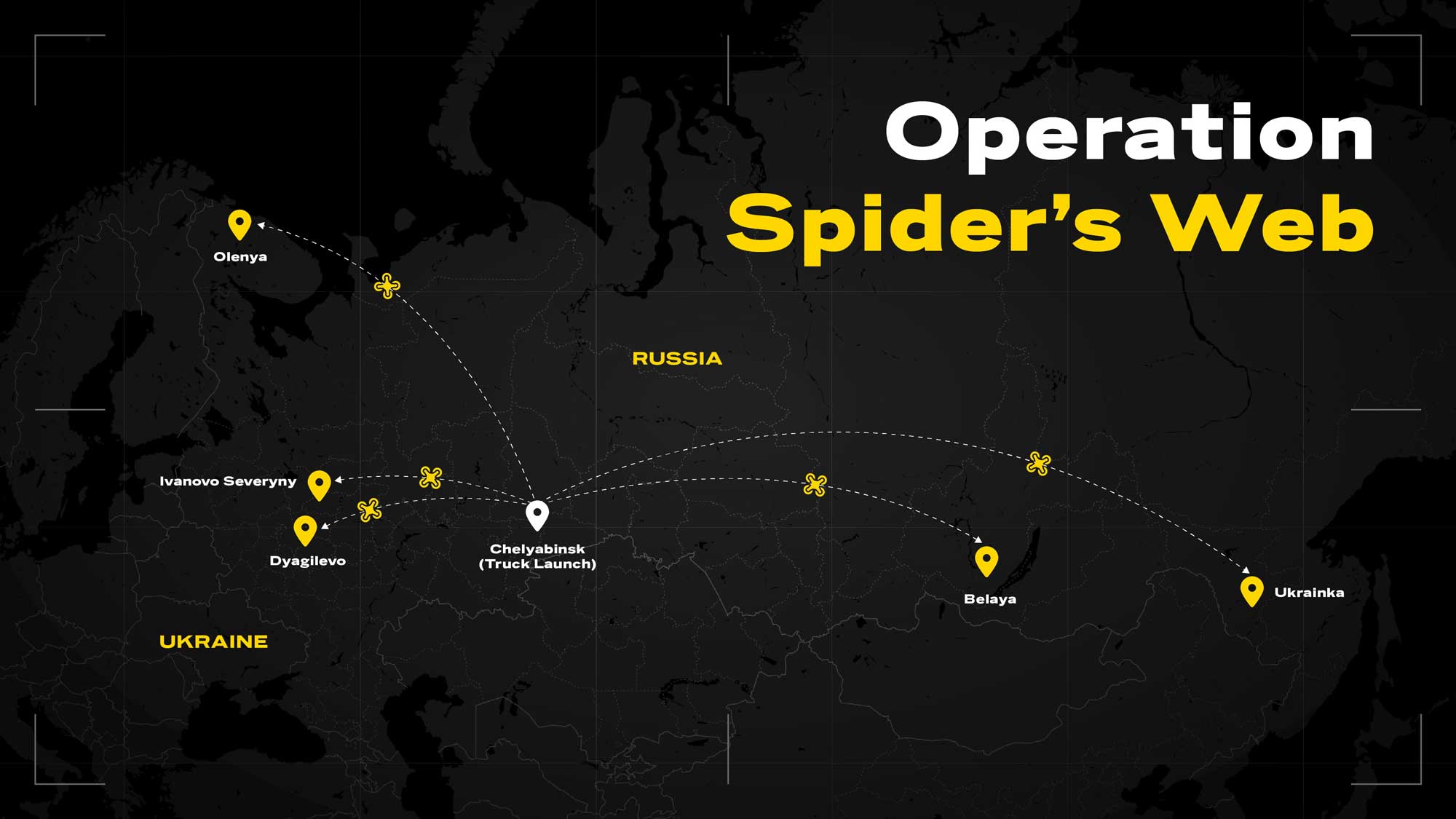
Twelve days later, Israel’s “Operation Rising Lion” operation demonstrated the power of prepositioned drones paired with a more traditional attack. Small explosive drones, planted months earlier, disrupted Iranian radar and communications, clearing the way for over 200 fighter jets, including advanced F-35s, to strike more than 100 military and nuclear targets. The result was a seamless integration of autonomous platforms and crewed airpower in a single, synchronized assault.
The EU’s €800 billion ‘ReArm’ initiative, running through 2027, lists drone and counter-UAS (cUAS) as a “pressing capability priority.” NATO allies have committed to raising defense spending to 5% of GDP, more than double the previous target. These investments acknowledge not only the threat from low-cost commercial copter drones but also the rise of advanced systems like fibre-optically controlled drones, immune to jamming¹, fixed-wing, DIY, insect-sized, spoofing² drones and more.
The implications are clear: airspace can now be breached without an attacker ever entering the target country. Drones can cross borders without using airfields, remain dormant for weeks or months, and strike with precision while operators stay undetected, unchallenged, and often untraceable.
This report draws on Dedrone’s operational datasets from 2024 and 2025 across Europe, the Middle East, and Asia, to examine evolving drone behaviors and tactics. It analyzes patterns in border crossings, night operations, manufacturer profiles, and detection methods, identifying how these behaviors are shifting and what they reveal about the next phase of the threat.
Section 1
Today, inexpensive and expendable or attritable drones are overturning more than a century of assumptions about air defense and reshaping how nations protect themselves. Real-world conflicts have proven this shift and exposed the limits of air defenses designed for conventional threats. Drones, especially when deployed in swarms or paired with real-time intelligence and traditional attack systems, can dismantle defensive systems before they even activate. These are not isolated anomalies — they are early demonstrations of a broader change in how military power is applied.
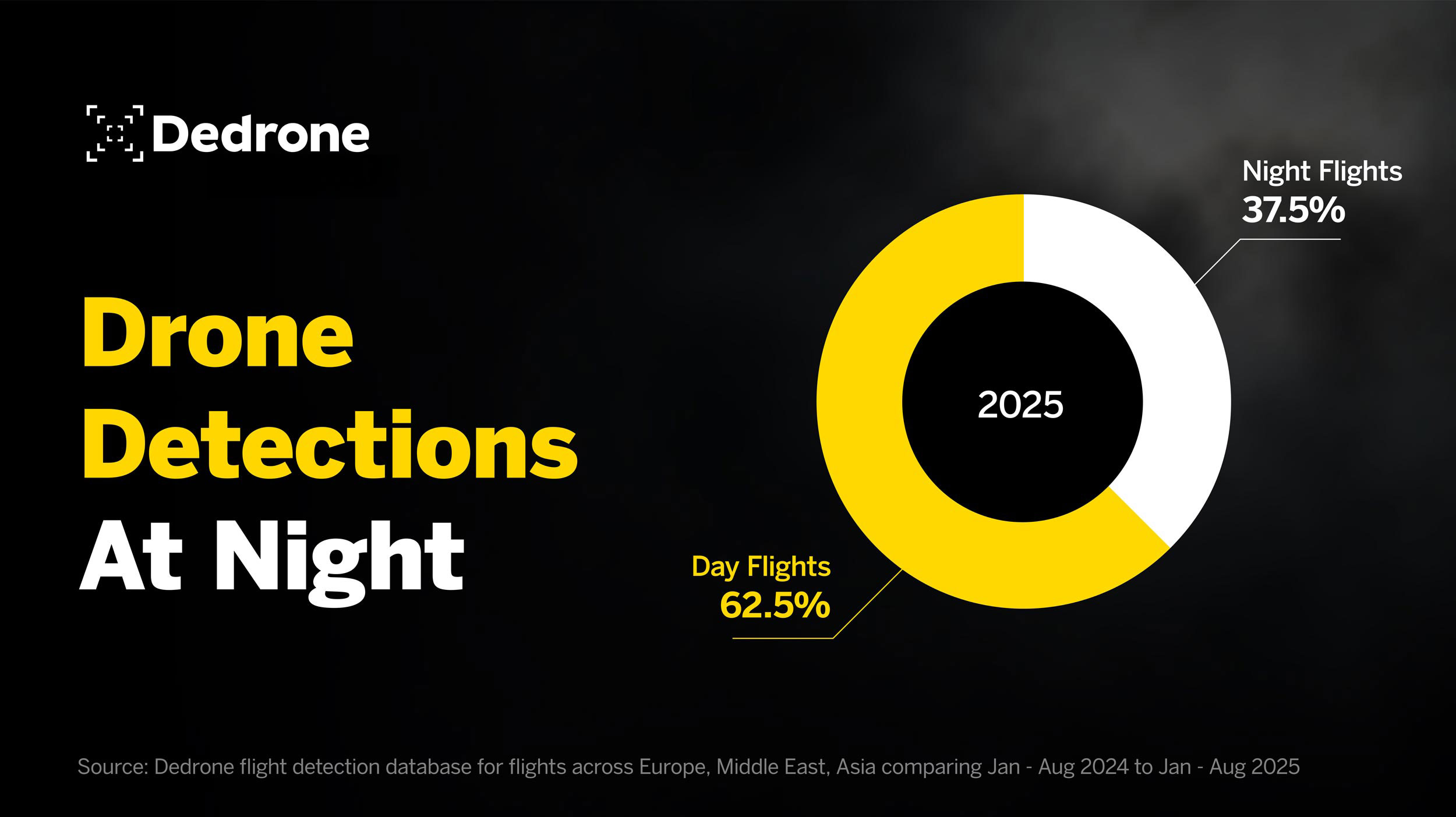
Dedrone’s 2025 network data confirms that these tactics are becoming routine. With only three months remaining in the year, 37.5% of detections across Europe, the Middle East, and Asia have occurred at night, indicating operators are deliberately exploiting reduced-visibility conditions to bypass traditional surveillance.
New technologies are further amplifying the threat. Drones equipped with electronic warfare (EW) capabilities can jam or spoof communications, disrupting both detection and countermeasures. Many operate quietly enough to avoid notice until it is too late, creating a persistent psychological pressure on those personnel charged with holding ground or physically protecting key assets. These loitering threats that are invisible, unpredictable, and capable of striking without warning.
Taken together, these patterns signal a strategic upheaval. The combination of low-cost platforms, stealth-focused tactics, and advanced counter-surveillance tools means that airspace can no longer be secured by traditional measures alone. Drones are not just adding a new layer to the threat environment, they are redefining it. This is forcing militaries to rethink how, where, and when defenses must operate. The countries that fail to adapt will face adversaries able to strike with precision, cross borders at will, and exploit vulnerabilities faster than legacy systems can respond.
Section 2
For decades, air defenses were expensive and built on the assumptions that threats would be both detected with time to react as well as worth meeting with equally expensive countermeasures. That logic has collapsed. Inexpensive, UAS now force militaries to either employ multimillion-dollar interceptors or improvise dangerous, close-range responses — both of which hand the advantage to the attacker.
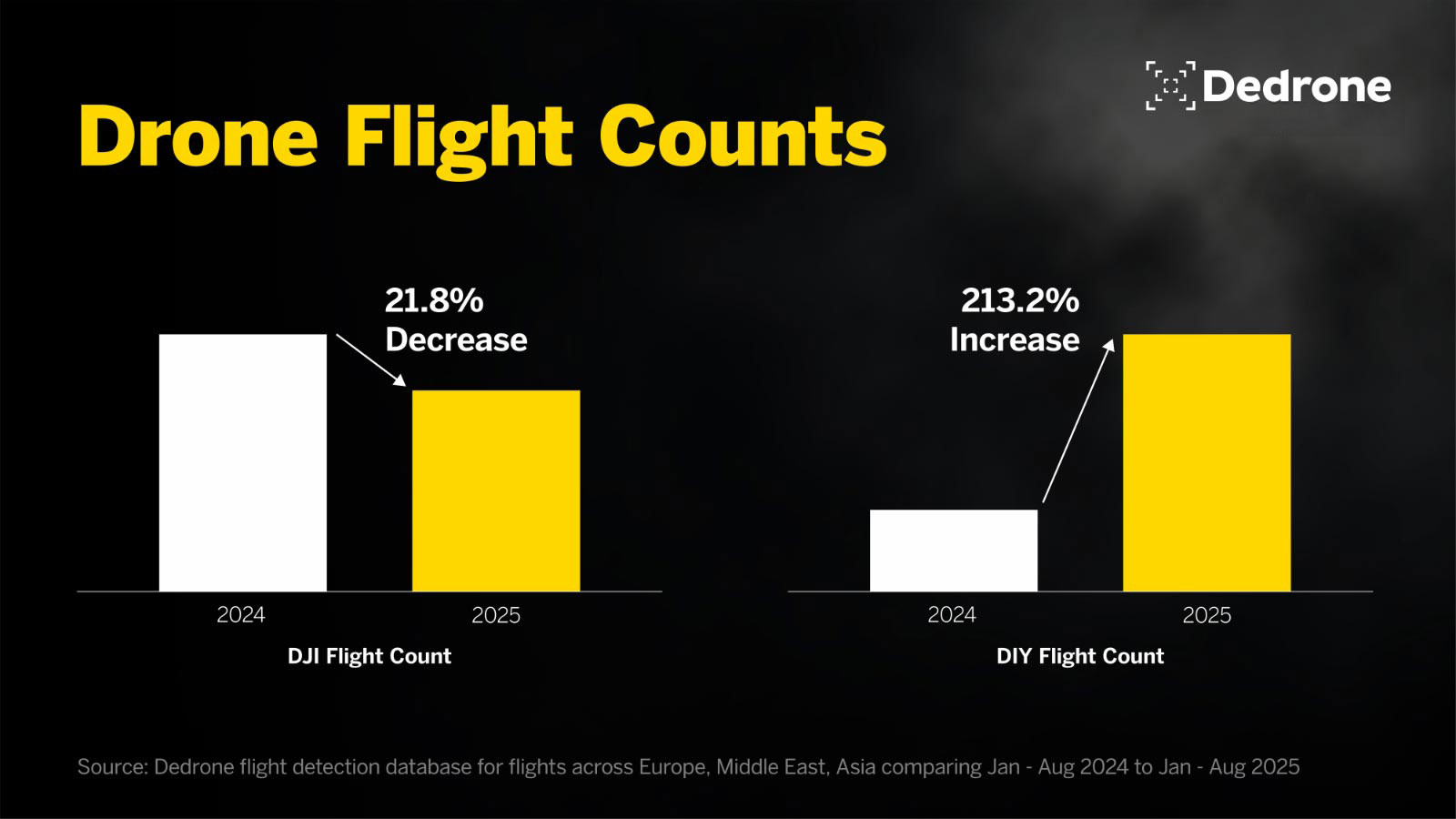
Dedrone’s 2025 data from Europe, the Middle East, and Asia shows that just three categories - DJI, Autel, and DIY builds - accounted for 94.70% of all detections:
The remaining 5.3% of detections are spread thinly across dozens of other manufacturers. This concentration means that today, the overwhelming majority of drones in operational theaters come from well-known, commercially available ecosystems, and they’re being used at scale.
Looking back at 2024 (Jan–Aug), DJI also dominated the threat picture but to a much greater extent. DIY has grown as have many smaller other drones that gained share. This shift toward diversity indicates the fast pace of evolution of drone threats as pilots expand their horizons to other, harder to detect, platforms.

With this narrow but growing set of platforms, the defender’s economics become even more lopsided if they fail to adapt. Consider:

Because attackers can mass-produce and replace these drones for a fraction of the cost it takes to stop them, the economic imbalance is unsustainable for defenders.
The concentration in DJI, Autel, and DIY is a problem, but it is also an opportunity:
Right now, the concentration of detections around DJI, Autel, and DIY builds looks like an opportunity for defenders: tune sensors, optimize countermeasures, and focus operational planning against the nearly 95% of known threats. But the reality is harsher. In this kind of warfare, even if defenses neutralize nearly all of that 95%, a single drone slipping through can cause outsized damage. That asymmetry does not disappear; it simply shifts. This is what makes the new battlespace so unsettling: defenders cannot afford to miss even once.
Section 3
Drone warfare is evolving at a pace that traditional defense systems were never built to match. What once required years of research, prototyping, testing and procurement can now be achieved in a matter of months, or even weeks, thanks to cheap components, global supply chains, and open-source knowledge. This isn’t just a technological shift, it’s a complete inversion of the old rules of air dominance, one where speed and adaptability matter more than size or cost.
Every breakthrough in drone capability has triggered an equally creative response from defenders, only to be met with yet another adaptation from attackers. Early off-the-shelf quadcopters were vulnerable to radio jamming. Pre-programmed drones bypassed this by eliminating the need for a live signal. GPS jammers appeared, so attackers adopted inertial navigation to fly without satellite guidance. Then came fiber-optic tethers, removing radio emissions entirely, making drones undetectable by conventional sensors. The cycle continued with FPV kamikaze drones, which turned consumer tech into precision-guided weapons, and swarms that overwhelm defenses through sheer volume.
These advances are no longer the domain of state militaries. DIY kits, 3D printing, and global online marketplaces mean insurgents, militias, and even criminal networks can field sophisticated aerial capabilities. The tools required, coding forums, consumer-grade parts, and a few thousand dollars, are far more accessible than the fleets of jets and trained pilots that defined air power for the last century+. The “minimum viable air force” is now a hobbyist’s project, and that reality permanently shifts the balance of power.
Artificial intelligence (AI) is supercharging this cycle. Generative AI and adversarial simulation allow operators to design, test, and refine novel drone tactics in virtual environments before they are ever flown. This means autonomous targeting, real-time swarm coordination, and adaptive mission profiles can be developed and deployed MUCH faster than traditional defense R&D can respond. Open-source AI models make these capabilities available not only to militaries but to non-state actors. Soon, autonomous drones could adjust their own routes mid-flight, respond to jamming attempts, or select alternate targets without any human input.
The speed of this evolution means governments are often reacting to yesterday’s threat while tomorrow’s is already airborne. Defense agencies no longer have exclusive control over the rules of air dominance. AI-driven, low-cost innovation gives adversaries the ability to challenge even the most advanced militaries and the advantage will go to whoever can adapt fastest. If defenders fail to match this pace, the skies will belong to the most agile, not the most powerful.

The image above is from Crazyswarm2, an open-source drone swarm AI project on GitHub. It provides code, documentation, and examples that make coordinated multi-drone flight accessible to anyone with basic skills. What once required state labs and defense budgets can now be learned and deployed by hobbyists or armed groups using free online resources. This open access accelerates the spread of swarm tactics and puts advanced aerial capabilities into the hands of non-state actors.
Section 4
The modern drone threat is not just different, it is more complex. Over 80% of 2025 detections in Europe, the Middle East, and Asia were identified via RF systems, but the growing number of RF-silent flights shows how quickly the detection challenge is evolving. Operators are now employing drones in more varied and sophisticated ways than ever before:
At the heart of this adaptability is modularity, the ability to swap payloads, navigation systems, or sensor manipulators to fit the mission. A single airframe can be a decoy, a jammer, and a weapon in the same operation. This versatility blurs the line between kinetic and non-kinetic warfare, complicating decision-making and delaying coordinated responses. Drones are no longer just tools of war, they are adaptable disruption platforms.
The foundations of traditional airspace security were built around previously known threats such as fast aircraft at high altitude, steady radio emissions, and radar signatures large enough to stand out from background clutter. Drones break all of those assumptions. They fly low and slow, often without RF signals, and present radar cross-sections as small as birds. This matters because RF detection has long been the backbone of CUAS operations. When that backbone weakens, the rest of the system is at risk. An RF-silent drone does not just evade one sensor, it can create a blind spot across an entire defense network. The fight is no longer just to spot drones, but to anticipate new configurations before they appear. Without that shift in mindset, defenses will remain one step behind attackers who can change shape overnight.
Even if RF-silent flights remain a minority for the near-term, their impact is disproportionate. They force defenders to rethink their sensor mix, retrain personnel, and rework response procedures. Each adjustment takes time and resources, which is exactly what hostile operators hope to exploit.
The drop in RF detections is a warning, not a footnote. It signals that the tactics we face are evolving faster than many defenses are adapting. If counter-UAS strategies remain anchored to an RF-first approach, a growing share of the threat will be missed. The future of airspace defense will belong to those who can detect drones regardless of the signals they emit.
Section 5
The next generation of drone threats will be defined less by the airframes themselves and more by the intelligence, connectivity, and tactics behind them. These systems are already moving from concept to prototype to battlefield at a pace that outstrips traditional policy, planning and procurement cycles. The coming wave of capabilities will challenge both how we detect drones, and how we defend against them.
Emerging threats fall into three broad categories:

These capabilities point to a fundamental shift: the fight will no longer be against individual drones but against complex, multi-domain operations that span air, surface, sub-surface, and land, often supported by electronic warfare such as jamming, spoofing, or digital sabotage. Defenses designed for one threat vector will fail when faced with many acting in concert. The advantage will go to those who can integrate sensors, interceptors, and decision-making across domains into an intelligent and networked line of detection linked to defense systems as quickly as the threat evolves. The battlefield of the future will belong to the side that can adapt not just to new drones, but to entirely new ways of employing them.
Section 6
The drone threat is evolving too fast for static, hardware-bound defenses. In a battlespace defined by autonomy, mass deployment, and hybrid tactics, the advantage will go to the side that can adapt in real time. Defending airspace in this new era means shifting from rigid systems to flexible, software-driven architectures that grow and change as quickly as the threat itself. The trajectory ahead makes this shift unavoidable, as three forces of automation, scale, and AI-driven adaptability are redefining how drones are used and how defenses must respond.
Dedrone already delivers on these requirements. Our systems are AI-software-driven, built on an open-architecture, and designed for networked detection and response defense strategies.
Conclusion
The rapid evolution of drone warfare has exposed a widening gap between emerging threats and the systems designed to stop them. Legacy air defenses were built for a different era, one defined by predictable, state-launched attacks and expensive, centralized platforms. Today’s battlespace looks nothing like that. Decentralized actors now deploy cheap, autonomous drones that launch in minutes, evade detection, and scale effortlessly. They can exploit radar blind spots, saturate defenses with swarms, and operate in the grey zone between peace and open conflict. In this environment, speed, adaptability, and control of the information loop matter more than sheer firepower. Securing airspace requires defenses that are not just stronger, but smarter, faster, and fully networked.
Winning this fight is no longer about jets or tanks. It is about real-time intelligence, adaptable platforms, and rapid iteration. Software-defined warfare rewards those who can sense, decide, and act faster than the threat. This is the future Dedrone is building:
Drones have already changed the rules. Defense must evolve at the same pace or faster. The next attack will not begin with a missile; it will begin with a drone. The data in this report is more than a snapshot of the present, it is an early warning system. Airspace defenses need to shift from reactive to predictive, giving operators the ability to counter tomorrow’s tactics before they become tomorrow’s headlines. In five years, the critical question will not be whether drones can strike. It will be whether we acted soon enough to stop them.
The next era of airspace defense will not be won by those with the largest hardware stockpile, but by those who can adapt the fastest. Flexibility, integration, and real-time iteration must replace static, single-purpose systems. Without that shift, defenses will lag behind watching tomorrow’s threat take shape while still reacting to yesterday’s.